How To Check Iptables Logs In Linux
Iptables -A INPUT -j LOG With syslog I could see the iptables logs doing this. If you want to change the file that IPTables logs to you need to.

Debian Why Iptables Drop All Packets Super User
Right-click on Windows Firewall with Advanced Security and click on Properties.

How to check iptables logs in linux. All the remaining incoming packets will jump to the LOGGING chain. If you dont know you can read our SSH tutorial. How do you Analyse firewall logs.
Iptables -L -n OR sudo iptables -L -n. This is such a crucial folder on your Linux systems. Open up a terminal window and issue the command cd varlog.
Iptables -A LOGGING -j DROP. Iptables -N SIP-Firewall iptables -A SIP-Firewall -s 11010002552552550 -j ACCEPT iptables -A SIP-Firewall -s 2049161164 -j ACCEPT iptables -A SIP-Firewall -s 63209144201 -j ACCEPT iptables -A SIP-Firewall -s 665414046 -j ACCEPT iptables -A SIP-Firewall -m string --string tel --algo bm --to 65 -j DROP iptables -A SIP-Firewall -m string --string OPTIONS sip --algo bm --to. Sudo nano etcrsyslogd10-iptablesconf.
Check Current iptables Status To view the current set of rules on your server enter the following in the terminal window. Introduction to Linux iptables. Log the incoming packets to syslog varlogmessages.
-varlogiptableslog. We can also define the source ip. Rule is condition used to match packet.
Iptables -I INPUT 1 -j LOG make sure to use -I instead of -A because this rule should be executed first before checking the other rules so 1 is used to place the rule first. It should be all zeros unless youve changed your firewall settings previously. It can be done in the configuration of the program that dispatches logs.
If you dont know thats another question Use tail -f on that file as you are attempting to reach the port from the other host. After enabling iptables logs. Chain is a collection of rules.
Connect to your server via SSH. This can clutter things up and make it hard to check the logs. Now lets take a peek into one of those logs.
Iptables -t table -P chain target options iptables -t table -E old-chain-name new-chain-name DESCRIPTION Iptables is used to set up maintain and inspect the tables of IP packet filter rules in the Linux kernel. In the iptables rule add a prefix that isnt used by any other kernel log. Open this file up in a file editor.
To check the status of your firewall and all rules enter. You can see the Windows firewall log files via Notepad. This chain as it is named first logs every single packet and then drops it.
Ive been trying journalctl and journalctl -f. Finally drop all the packets that came to the LOGGING chain. Tables is the name for a set of chains.
To List all rules in the selected chain use the -L option. A listing of log files found in varlog. Sudo iptables -L -v.
Journalctl alone shows a lot doing a grep -v of what I am not interested I still cant see anything about iptables. Sudo iptables -L -v -n more. To list all rules for INPUT tables.
Several different tables may be defined. For instance this firewall can be installed to your Linux Dedicated or Virtual Server to secure your server workloads. Iptables is a program that utilizes policy chains to configure the IP packet filter rules of Linux kernel firewall in order to allow or block traffic.
Iptables -A INPUT -j LOGGING. To list all IPv4 rules. Go to Windows Firewall with Advanced Security.
If you need to specify a different table use the t option followed by the name of the table. The first line checks the log data for the word iptables. You should take notice of the FORWARD chain.
Now issue the command ls and you will see the logs housed within this directory Figure 1. It will list out how many packets your system have accepted and sent till now. The iptables are used to manage setup and examine the IP packets in the Linux kernel.
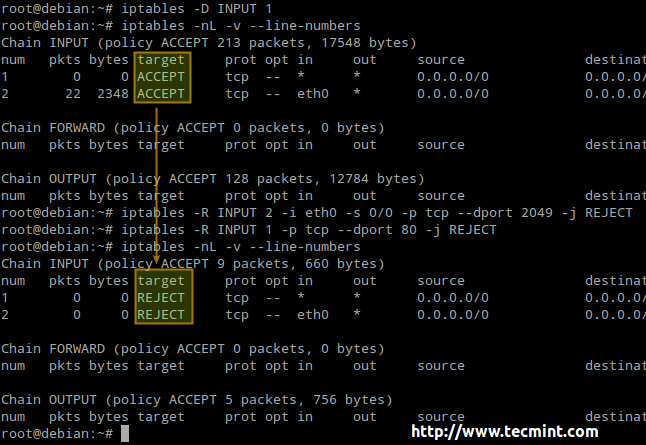
Viewing all iptables rules in Linux The syntax is. How do you check if iptables is enabled. If no chain is selected all chains are listed.
Execute the following command one by one. Add the following two lines. How to Enable Logging in Iptables on Linux Enable Iptables LOG.
This line is explained below in detail. Check Your Iptables Status sudo iptables -L -v The above command will show you the current status of your iptables. FORWARD chain iptables -I FORWARD 1 -j LOG OUTPUT chain iptables -I OUTPUT 1 -j LOG.
Check following log files to view logs generated by iptables as per. In the Linux operating system iptables is a utility or tool to manage the firewall rules in the environment. And appends it into the varlogiptableslog file.
To list all tables rules. As every other iptables command it applies to the specified table. Service or maybe just the service iptables status command depending on your Linux distribution.
Iptables -I OUTPUT -s 19216810010 -p tcp --dport 22 -j LOG --log-level info You can find the log output wherever you have kernel logs directed to. Iptables -S iptables --list iptables -L iptables -S TABLE_NAME iptables --table NameHere --list iptables -t NameHere -L -n -v --line-numbers Print all rules in the selected chain sudo iptables -S sudo iptables -S INPUT iptables -S OUTPUT How to list rules for given tables. The firewall matches packets with rules defined in these tables and then takes the specified action on a possible match.
Similarly we have one more tool to manage the firewall rules on the Linux ie firewalld. To list all IPv6 rules. Iptables on Linux provides logging functionality however by default it will get outputted to the varlogmessages log file.
The -n option help to print IP addresses and port numbers in numeric format. Sudo apt-get update sudo apt-get install iptables. Sudo iptables -L INPUT -v -n.
Iptables -A INPUT -s 19216811024 -j LOG --log-prefixnetfilter Following the example set by 20-ufwconf create a file under etcrsyslogd00-my_iptablesconf containingmsgcontainsnetfilter -varlogiptableslog. How to Install and Use Iptables Linux Firewall. Reset Your Iptables Rules.
Lets say if a user attempts to SSH into your server iptables will try to match the IP address and port to a rule in. Tail -f varlogsyslog grep kernel With systemd I cant find a way to see what is failing. Each table contains a number of built-in chains and may also contain user-defined chains.
Check the status of your current iptables configuration by running. Save the file and exit the editor. You can also query iptables with the command iptables -L that will list the active rules.
Open the terminal app or login using ssh. Iptables -N LOGGING. Configure iptables in Linux By default these commands affect the filters table.
You can however easily check the status of iptables with the command systemctl status iptables. Iptables -A INPUT -s zzzz32 -j LOG_AND_DROP iptables -A INPUT -s yyyy32 -j LOG_AND_DROP iptables -A INPUT -s aaaa32 -j LOG_AND_DROP This will take any packet matching those source addresses and send it to the LOG_AND_DROP chain. How set iptables rule in Linux.
That rule comes before the one you want to test. Similarly you can execute the same command for other chains. Create a new chain called LOGGING.
Iptables on Linux provides logging functionality however by default it will get outputted to the varlogmessages log file. Iptables is a command line interface used to set up and maintain tables for the Netfilter firewall for IPv4 included in the Linux kernel. How to list all iptables rules on Linux.
We can simply use following command to enable logging in iptables.
How To Setup An Iptables Firewall To Enable Remote Access To Services In Linux Part 8

Komentar
Posting Komentar